It looks as though the CIA could possibly break into a most cell phone or PC systems, in any event as indicated by the stolen reports discharged identified with cybersecurity by WikiLeaks.
Regardless of whether you have anything to hide or not. It’s a decent update that in a computerized age, keeping your life private requires some work.
Here’s a rundown of some cybersecurity related things everybody ought to do as of now to keep their data generally classified, in addition to four more for the really distrustful:
Table of Contents
Just utilize secure web programs
Search for sites that utilization the safe variant of the web protocol. You can judge by taking a gander at the URL. Which ought, to begin with, HTTPS as opposed to just HTTP. It remains for Hypertext Transfer Protocol Secure and shields vindictive outsiders from embeddings code onto the site.
Turn on two-figure validation
This is an irritating stride that comes in the wake of writing in your secret key. It sends a code to your advanced mobile phone or landline or sometimes email. You input the code – the second consider the validation procedure – and you’re ready.
While it appears like a bother, it’s really a to a great degree capable approach to shield anybody however you from getting into your records. They’d need to have stolen your ID and login as well as your telephone.
You ought to turn two-calculate confirmation on for each application, program, and gadget for which it’s accessible. It’s a little band for you to hop through yet a colossal divider for programmers, and would-be spies, to overcome.
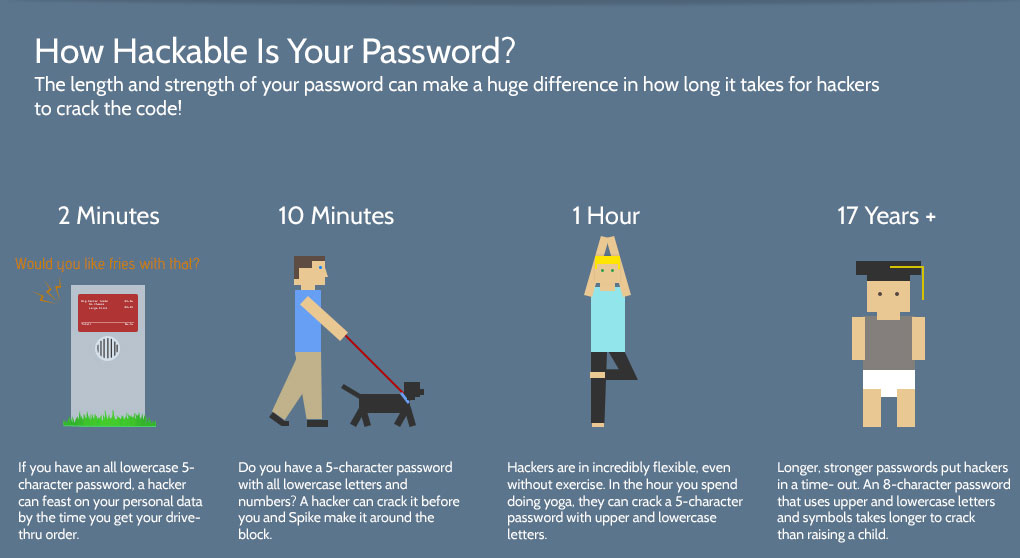
Utilize solid passwords for cybersecurity
There are powerless passwords and after that, there are insane feeble passwords. As per an overview by Keeper, which makes secret word administration programming, 17% of clients have 123456 as their watchword, trailed by 123456789 and qwerty. In any event, set up a battle! Pick solid passwords or agree to accept a watchword administration program that will make them for you.
Use current working operating system
A number of the vulnerabilities itemized in the WikiLeaks reports are more established and target-dated frameworks. It’s completely conceivable that the CIA has more current instruments for fresher projects, however, we don’t have the foggiest idea. What we do know is that the more extended a working framework or program is around, the more vulnerabilities in it that are found and misused. To utilize the latest form of whatever working framework you incline toward (Microsoft, Apple, or Linux for the most part) and when another one turns out, don’t hold up always to switch.
Introduce security updates and patches
When you get another telephone or PC or introduce another operating system. Set it up to consequently refresh with security patches. In the event that there’s no program refresh accessible, check intermittently to check whether anything new is accessible.
Utilize a security program for cybersecurity
There are many out there, from allowed to ones you pay for. While it’s impossible they’d keep the CIA out of your framework, they’ll make a decent showing with regards to keeping ordinary programmers away and might make it somewhat harder for spies to get to you.
Use encrypted messaging software
There’s no proof the CIA was utilizing the devices portrayed in the WikiLeaks records to keep an eye on Americans, which would be illicit under U.S. law as the CIA can’t work inside the United States. So, on the off chance that you truly need to keep your life secret, here are a couple of more things you can do.
Mainstream programs incorporate Signal, Telegram, and WhatsApp. The WikiLeaks reports asserted that the CIA had a program that permitted it to perceive what clients were writing on specific telephones running the Android working framework, yet they hadn’t possessed the capacity to break the encryption of the projects themselves.
Install a camera cover on your PC and telephone
This shields anybody from having the capacity to surreptitiously turn on your camera and utilize it to record you. At programmer gatherings, it’s regular to see little bits of paper taped over PC cameras, or minimal plastic sliding spreads that permit them to cut off the focal point when they’re not utilizing it. It’s a low-tech settle for a cutting-edge issue.
Utilize a landline
While it’s moderately paltry to bug somebody’s telephone. There are solid legitimate assurances around doing as such in the United States, including the prerequisite that those doing the pestering get a court to arrange. So making an approach a landline is more secure, or possibly more legitimately ensured. Then making an approach a mobile phone. It likewise doesn’t leave an advanced trail as writings or emails do.
Unplug and turn off your devices
For the really suspicious, an ideal approach to ensure the gadgets that encompass. You aren’t keeping an eye on you is to unplug them or turn them off.
So these are some points, we covered about cybersecurity. Finally, think about what you’re giving away for free? How much information do you voluntarily turn over to websites, apps, and online services every day?